Managed Cloud Monitoring for Amazon Web Services
With so many devices, users, and systems to manage on the network, significant blind
spots can emerge.
VectorUSA provides comprehensive visibility into your Amazon Web Services (AWS) resources and the security expertise you need to rapidly detect and respond to threats across your on-premises and AWS cloud deployments. We will help you comply with regulatory mandates like PCI, HIPAA, and SOX. Discover how VectorUSA can help you make sense of risk and strengthen your security environment. Contact us now.
Centralized Monitoring for Your AWS Infrastructure
VectorUSA provides comprehensive visibility into your AWS resources. Our AWS monitoring solution provides:
Customizable threat detection logic
Customize monitoring and alerting based on your AWS environment’s specific needs.
24x7 Concierge Security access
24x7 monitoring delivered by industry-leading experts to detect suspicious activity in your AWS environment.
Comprehensive AWS coverage
Centralized analysis of activity from CloudTrail, CloudWatch, GuardDuty, AWS WAF, EC2 instances, and more.
AWS security posture management
Scan and inventory cloud assets, and benchmark and improve security posture.
Host vulnerability scanning
Extract vulnerability information from hosts in your AWS environment.
CIS Security Controls benchmarking
Evaluate the security controls in your AWS hosts against industry standards.
Security Agent for EC2 visibility
Enable agent-based collection of Windows Event logs for enhanced visibility into your EC2 instances.
Detailed weekly reporting
Concierge-delivered weekly reports of activity across active AWS services
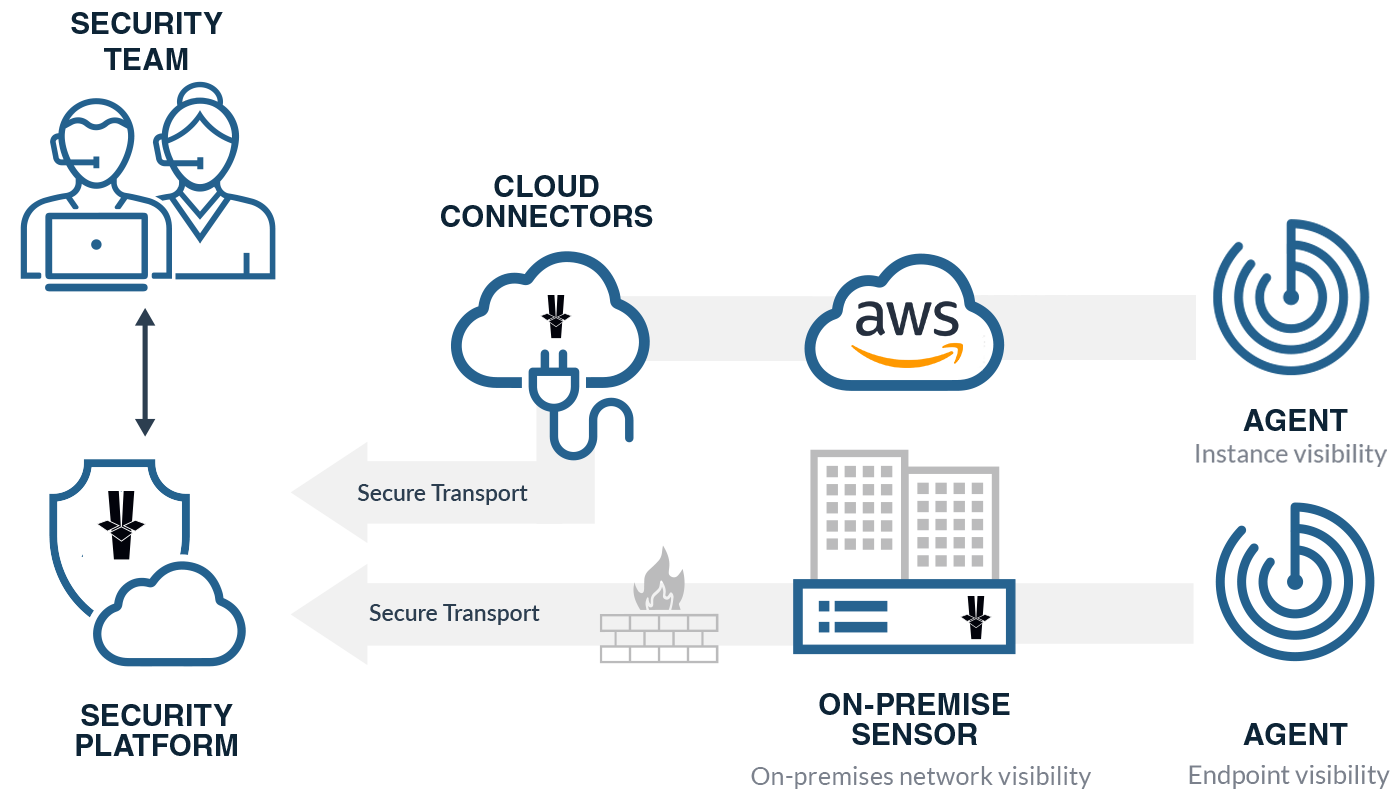
Rapidly Detect Attacks
Below are a few examples of the types of AWS activity that Arctic Wolf enables you to detect. VectorUSA alerts come with in-depth remediation context and guidance.
Detect suspicious AWS resource usage
- Unauthorized access to AWS web console
- Instance stop/reboot/terminate activity
- Massive resource deletions
- User profile updates
- Unusual instance detection
- Upload/delete certificates
Detect misconfiguration and inadvertent exposure
- Suspicious AWS administrative actions
- Public S3 bucket detection
- Creation of new users and security groups
Detect persistence and targeted attacks
- Brute-force login attacks
- Unexpected AWS service activity
- Concurrent access from multiple geographies
- Sign-ins from blacklisted IPs
To learn more about VectorUSA's SOC-as-a-service call us at 877.569.8800 or request a consultation now.
- Copyright © 2026 VectorUSA
- Terms of Service & Privacy Policy
- Your California Privacy Choices